Everything you need to know about DDoS attacks
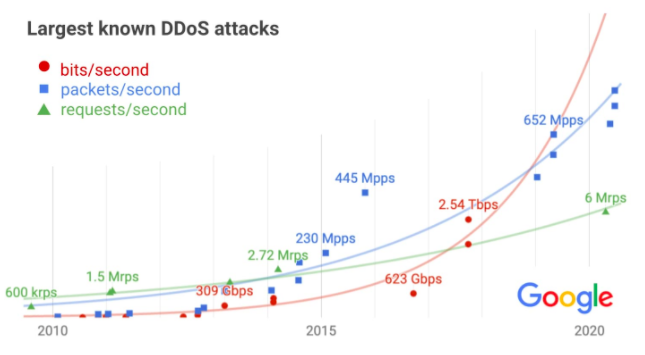
The Google Cloud team revealed recently that in 2017 they managed to push back the largest DDoS attack recorded to date. It clocked at 2.54 Tbps but had no impact. "The largest DDoS attack in the history" may sound scary but there is nothing to worry about since most companies are prepared for this kind of attack. How's the situation in CloudAccess.net? Most of the time DDoS attacks are small, and our network can absorb the hit while server admins resolve the issue, resulting in little to no downtime for our clients.
What is a DDoS attack?
DDoS is an abbreviation from "Distributed Denial of Service". Essentially, a DDoS attack is an attempt by many computers (usually controlled by a primary computer) to use up all the network resources available on a server, limiting website availability for intended users. If the DDoS attack is large enough, visitors experience a lag, and legitimate traffic cannot get through because bad traffic is flooding the Internet connections. The DDoS attack isn't a new phenomenon on the Internet. Many popular hosting providers are susceptible to DDoS attacks. As we can read the Google blog „Security threats such as distributed denial-of-service (DDoS) attacks disrupt businesses of all sizes, leading to outages, and worse, loss of user trust. […] With a DDoS attack, an adversary hopes to disrupt their victim's service with a flood of useless traffic. While this attack doesn't expose user data and doesn't lead to a compromise, it can result in an outage and loss of user trust if not quickly mitigated."
How the attack on Google was carried out? „Our infrastructure absorbed a 2.5 Tbps DDoS in September 2017, the culmination of a six-month campaign that utilized multiple methods of attack. Despite simultaneously targeting thousands of our IPs, presumably in hopes of slipping past automated defenses, the attack had no impact. The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us. […] It remains the highest-bandwidth attack reported to date, leading to reduced confidence in the extrapolation."
How CloudAccess.net handles DDoS attacks?
Our admins monitor our network consistently and we know immediately when an attack occurs. We jump into action by working with our upstream provider to search our core Internet routers for the IP address and server that is being attacked. Once we do this, the attacked server is taken down, effectively stopping the attack so normal traffic can resume for the rest of the network. This can be done fairly quickly. In a more simple DDoS attack - an attack from one machine - we can simply block that single IP from entering our network. In a larger DDoS attack, however, tens of thousands of IP addresses may be entering the network, and it's inefficient to try to identify and block each attacker. Instead, we completely dump the IP address that is being attacked and bring the network back to being operational.
Learn more about Bolt-DNS
At CloudAccess.net, we've built a very special DNS network aptly named "Bolt-DNS". Bolt-DNS is a distributed DNS network that allows us to handle very large volumes of traffic even during a DDoS attacks. Our Bolt-DNS network will distribute the traffic evenly during these attacks, and it quickly reacts by working with our DNS data centers to stop or block any denial of service attacks. We have cached networks that would continue to route mail even on the largest of network attacks. If you're looking for more reliable hosting, email and DNS services, look no further than CloudAccess.net. If you own a domain name you should be using Bolt-DNS. Improve the speed, SEO and security of your website and experience the fastest supported DNS network available.
More info: https://www.cloudaccess.net/bolt-dns.html
Please feel free to contact us directly if you have any questions.